Latest news
Privilege Escalation and RCE Vulnerabilities for Multiple ABB Appliances [ASPECT, Matrix, Nexus]. (CVE-2023-0635 / CVE-2023-0636)

Prism Infosec recently identified two high risk vulnerabilities within the ABB Aspect Control Engine affecting versions prior to 3.07.01. The two vulnerabilities discovered could result in remote code execution (RCE), and privilege escalation within ABB’s Aspect Control Engine software.
Background
During a recent security testing engagement, Prism Infosec discovered an ABB Aspect Appliance through traditional enumeration techniques. A Google search revealed that this is a building management control system and this instance it was misconfigured to be publicly available to the Internet.
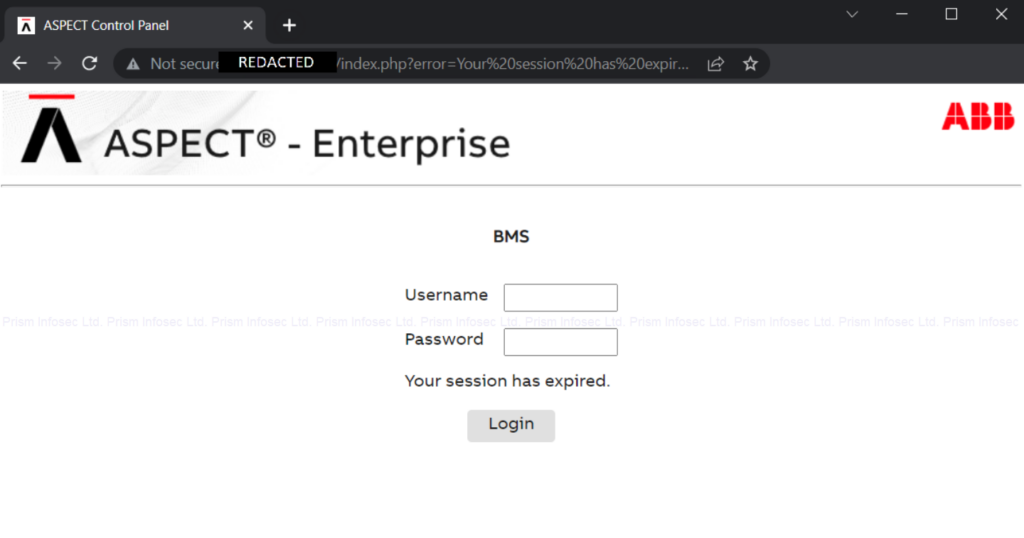
Typically, administrative interfaces should not be externally accessible over the Internet unless absolutely necessary. Where this is unavoidable, they should require a secondary layer of authentication such as VPN Access, IP address whitelisting with further controls such as Multi-factor Authentication (MFA).
Prism Infosec gained initial access to the admin interface by using the default credentials documented in the Aspect Control Engine’s publicly available user manual.
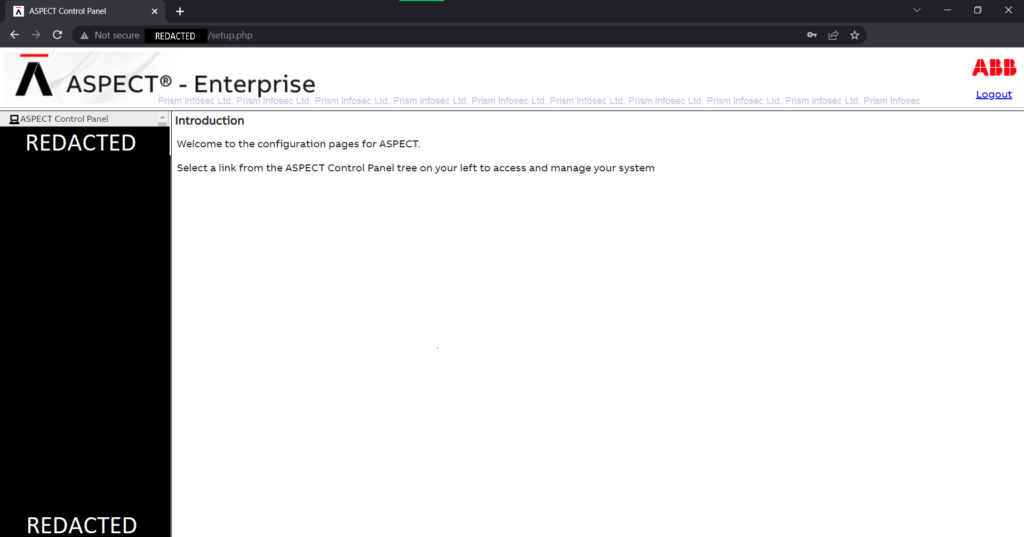
Exploitation
Following this access, Prism Infosec were able to identify that the Network Diagnostic function of the ASPECT Appliance was vulnerable to Remote Code Execution, which allowed us to gain access via a reverse-shell to the underlying Linux Operating System and associated internal network infrastructure.
CVE-2023-0636 – Remote code execution
The vulnerability here was possible due to the fact that the ping host functionality allowed for the appending of Linux commands to an IP address.
Because of this it was possible to host a shell file from Prism Infosec’s internal testing server and serve it to this web server’s htmlroot directory.
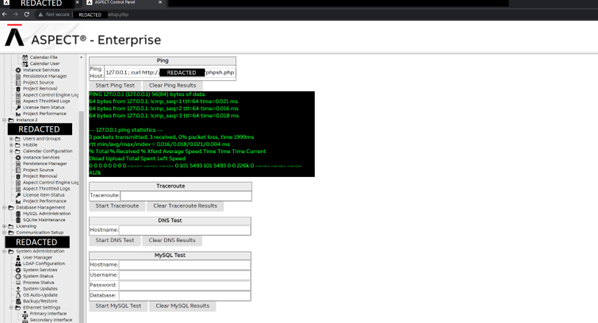
This PHP shell file allowed for remote connectivity to the ASPECT-Enterprise Application’s underlying system.
CVE-2023-0635 – Escalating from apache user to root.
After further investigation, Prism Infosec identified an unintended privilege escalation vulnerability, built into the underlying OS of the ABB Appliance. This then allowed the user to escalate to a root account.
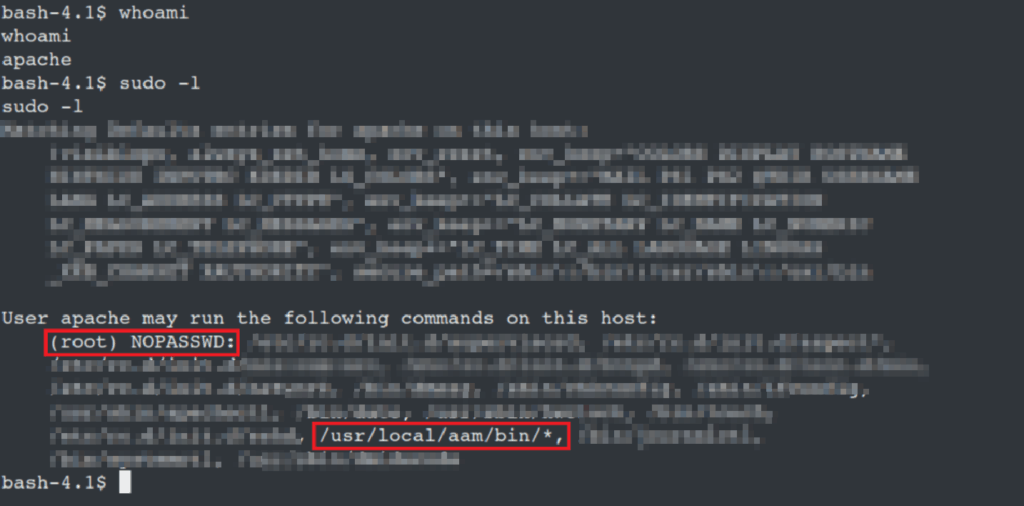
Once initial access was achieved, a check against the privileges revealed that the software was running as the ‘apache’ user, a relatively low-level user with limited functionality.
By using sudo -l it is possible to list what sudo permissions this low-level user has, take note of the /usr/local/aam/bin/* entry here at the bottom of the (root) NOPASSWD: section. A script was identified within this directory was called: copyFile.sh.
Root access achieved
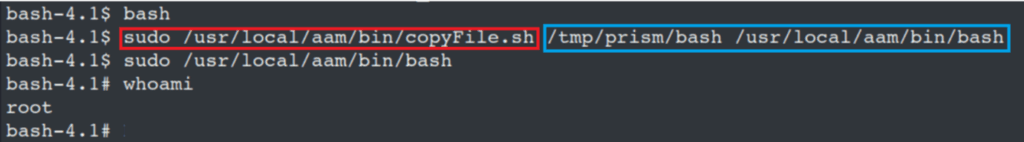
Because this directory did not require a password to be called as root, it was possible to copy /bin/bash into here, and sudo /usr/local/aam/bin/bash which allowed Prism Infosec to escalate to a root account.
The possibilities here are endless for an adversary, from exfiltrating local data, to enumerating and moving laterally through the internal network.
To summarise, Prism Infosec went from an external IP address open to the internet, to a rooted Linux system, inside an internal network.
Resolution
Prism Infosec quickly made our client aware of these vulnerabilities and disclosed to ABB the findings within their software shortly after. We were delighted to see both parties quickly acknowledging and acting on these issues, from the client ensuring these levels of access were disabled and ABB to patching and releasing an update and advisory to their clients.
Credits and References
- CVE-2023-0635 – Privilege escalation to root was discovered by George C
- CVE-2023-0636 – Remote code execution was discovered by Karolis N
CVE-2023-0635 Privilege escalation to root
The successful attacker can open a shell and escalate access privileges to root.
CVSS v3.1 Base Score: 7.8
CVSS v3.1 Temporal Score: 7.4
https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:F/RL:W/RC:C
CVSS v3.1 Vector:
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:F/RL:W/RC:C
NVD Summary Link: https://nvd.nist.gov/vuln/detail/CVE-2023-0635
CVE-2023-0636 Remote code execution
The successful attacker is able to leverage a vulnerable network diagnostic component of the ASPECT interface, to perform Remote Code Execution.
CVSS v3.1 Base Score: 7.2
CVSS v3.1 Temporal Score: 7.0
https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H/E:F/RC:C
CVSS v3.1 Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H/E:F/RC:C
NVD Summary Link: https://nvd.nist.gov/vuln/detail/CVE-2023-0636
Timeline
- Vulnerabilities discovered during the assessment: [05/10/2022]
- Vendor Informed: [07/10/2022]
- First Meeting with ABB and Prism Infosec: [11/10/2022]
- Final Meeting with ABB and Prism Infosec: [22/05/2023]
- Vendor Confirmed Fix, and communicated to customers: [01/06/2023]
- CVE Assigned: [05/06/2023]
- Prism Infosec Blog Post: [05/06/2023]